6 Penetration testing types to discover
Did you know that by the end of 2023, almost 70% of the world’s population was using smartphones?
With all your personal information collected in your pocket, sensitive data like GPS locations, contact lists, and email addresses can easily be compromised.
To protect your users from hackers' attacks and increase trust in your application, you should regularly conduct penetration tests.
In this article, we will explore 6 Penetration testing types and how you can perform them. Let’s start!
We can help you drive software testing as a key initiative aligned to your business goals
What is Penetration testing?
A penetration test, or pen test, is a simulated cyberattack on a computer system, website, mobile app, etc, conducted with permission to assess its security. During a pen test, experts use the same tools and methods as real attackers to identify and show the potential impact of any weaknesses. These tests mimic various possible threats, checking if the system can withstand attacks both from:
- within (by authenticated users) and
- from the outside (by unauthenticated users).
With a well-defined scope, a pen test can thoroughly investigate any part of a system.
Different approaches to Penetration testing
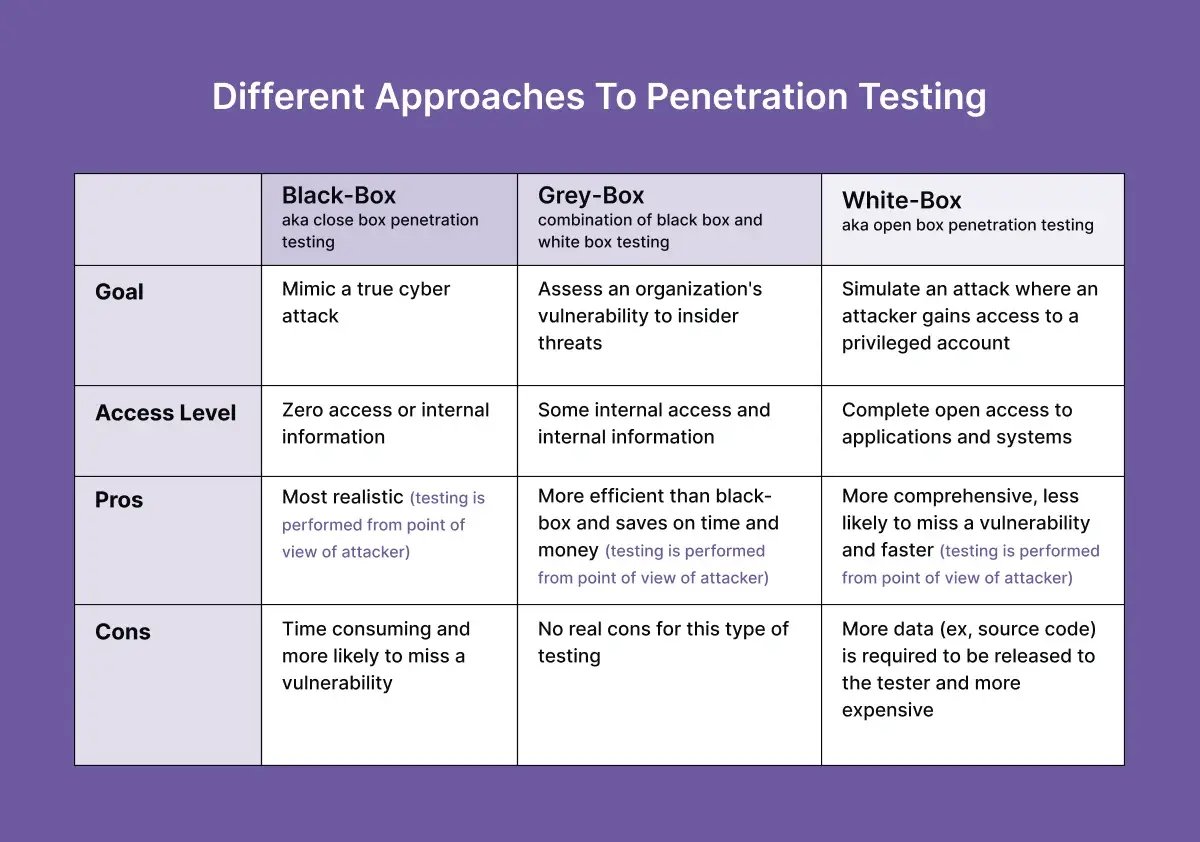
Penetration testing is an indispensable practice for checking a system's security. Statistics show that 75% of companies conduct penetration tests to evaluate their security posture or meet compliance requirements. Furthermore, 57% of these companies use penetration tests to enhance their vulnerability management programs.
When it is done correctly, it reveals the system's weaknesses. Penetration testers typically use three main approaches for different types of tests:
Black Box Penetration Test
In black box testing, the penetration tester evaluates the security of an application or system without any prior knowledge about it, not even the operating system or application type. The tester uses the same tools and techniques that a hacker would use.
This method is the most challenging because it requires a high skill level and only the resources an attacker would have. However, it is the best way to test the overall security of a system.
White Box Penetration Test
White box pen testing involves the tester having complete knowledge of the source code and environment. Instead of exploiting vulnerabilities, the tester focuses on understanding how the application works and attempts to break into it using that knowledge.
This is the opposite of black box testing, where the tester has no access to the source code.
Grey Box Penetration Test
Gray box testing provides the tester with partial knowledge of the target environment, such as network diagrams, documentation, or partial internal network access.
This gives the tester more insight than in black-box tests but less than in white-box tests.
Gray box testing is typically done early in a program to identify potential vulnerabilities and understand how much information an attacker could access.
6 Penetration Testing Types
Selecting the suitable penetration testing method depends on various factors, such as:
- The scale of your company,
- The intricacy of your IT framework,
- Regulatory obligations and
- Nature of your business activities.
Below are the most common penetration testing types, which you can use separately or in combination.

1. Wireless Penetration Tests
Wireless network penetration testing, also known as network security testing, evaluates a computer network's vulnerability to potential intrusions. This involves identifying flaws in the system or assessing the risk of hackers' attacks.
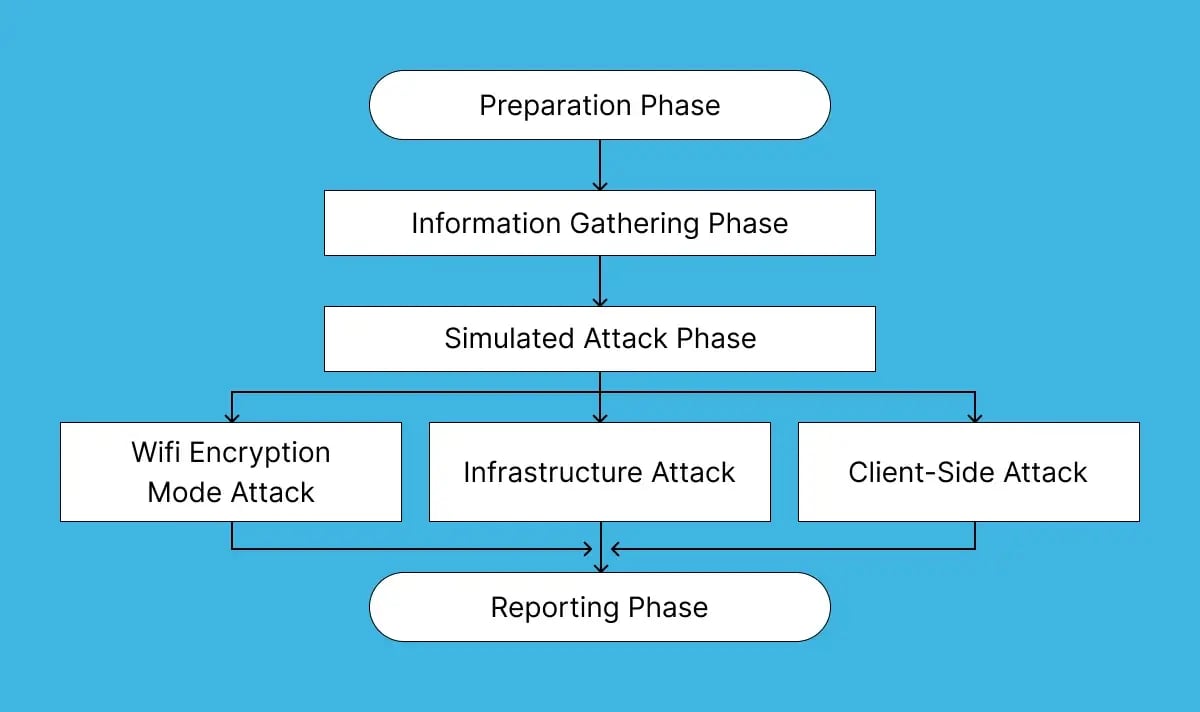
Wireless networks are among the most popular targets for cybercriminals, but security teams still often overlook them, leading to poor password and permission settings. Penetration testers address these issues by:
- Attempting to brute-force passwords
- Exploiting misconfigurations
- Ensuring protection against denial-of-service (DoS) attacks, which flood sites with traffic to force them to crash.
This type of testing is particularly valuable for networking companies handling large volumes of data and cloud companies that depend on secure networks.
2. Network Penetration Tests
A network penetration test is a process of identifying security flows in applications and systems by intentionally using different techniques to evaluate the network's security. There are two types of Network testing:
- External Tests – Testers use publicly available information to exploit an organization’s external assets. The goal is to understand how vulnerable the organization's external defenses are to outside attacks.
- Internal Tests – Testers simulate attacks originating from within the organization. They focus on scenarios involving a malicious insider or compromised internal network, assessing how well internal systems handle exploitations, lateral movements, and privilege escalations.

Since the stakes are high if an attacker breaches the network, penetration testers employ various techniques to identify vulnerabilities, including:
- Bypassing firewalls
- Testing router security
- Evading intrusion detection and prevention systems (IDS/IPS)
- Scanning for open ports and proxy services
- Examining all potential network vulnerabilities.
3. Mobile Penetration Tests
As the number of apps that we use every day that handle sensitive data has increased (e.g., mobile payments and healthcare apps), penetration testing has become more sophisticated, covering both Android and iOS apps.
The Mobile application penetration test checks a mobile app’s security weaknesses and reports them to the developers for fixing. The testing can range from basic functional checks to in-depth security assessments to:
- access sensitive data and
- disrupt the app’s functionality to uncover flaws.
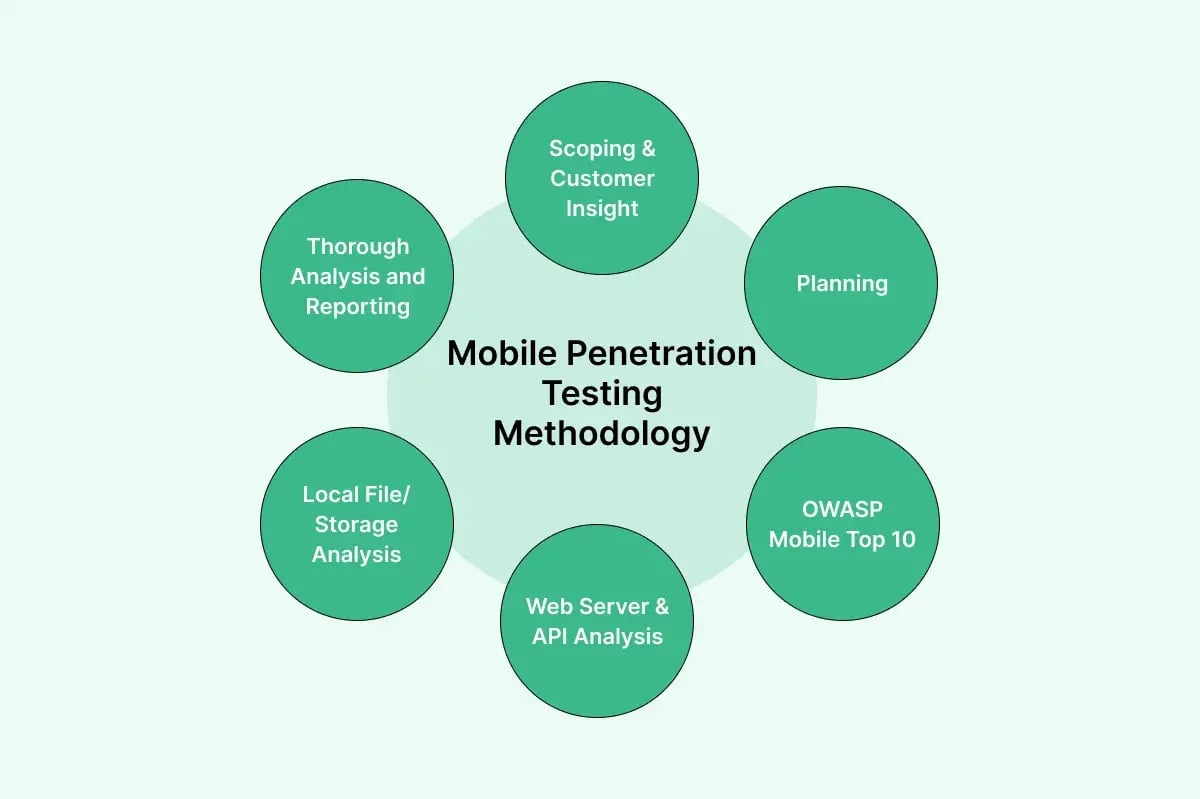
To avoid a high churn rate and establish credibility in your app, you should conduct these tests before releasing the app to the public and after any major updates since it:
- Provides credible evidence of vulnerabilities.
- Allows developers to resolve or mitigate issues before release.
- Reduces the likelihood of glitches and security breaches.
Mobile penetration testing is especially important for companies developing mobile apps for games, shopping, payments, etc.
4. Social Engineering Penetration Tests
Social engineering penetration test evaluates the security awareness of a company's employees by simulating attacks to identify potential vulnerabilities.
This type of testing involves creating scenarios where an attacker tries to trick employees into revealing sensitive information or granting access to secure systems.
Attackers usually contact workers through email, calls, social media, and other channels. Conducting these tests can help you:
- Identify weaknesses in both physical and digital security measures.
- Improve employee awareness of best security practices.
- Detect security gaps that could be exploited by attackers.
Social engineering penetration testing can help employees understand the risks of attacks, improve their handling of sensitive information, and, as a result, prevent them. This type of testing is beneficial for companies seeking an external perspective on their security measures and protocols' effectiveness.
5. Web Application Penetration Tests
Web-based application penetration testing is a step no organization should miss. Online threats are constantly evolving, and new applications often use open-source code, which has several challenges:
- Code isn’t always thoroughly checked for security.
- New threats continuously emerge, finding ways to exploit web applications.
During web application testing, hackers try to identify and exploit vulnerabilities, aiming to compromise the application and report the potential consequences.
Web application tests cover:
- Web apps, browsers, ActiveX, plugins, Silverlight, scriptlets, and applets.
- Various programming languages like Java, PHP, .NET, and others.
- Application programming interfaces (APIs), XML, MySQL, Oracle, and other systems.
- Mobile web applications that need testing in their specific environments.
These tests are complex because of the numerous endpoints and the interactive nature of web applications when they are live. So, as with any other mentioned penetration type, it requires careful planning and execution.
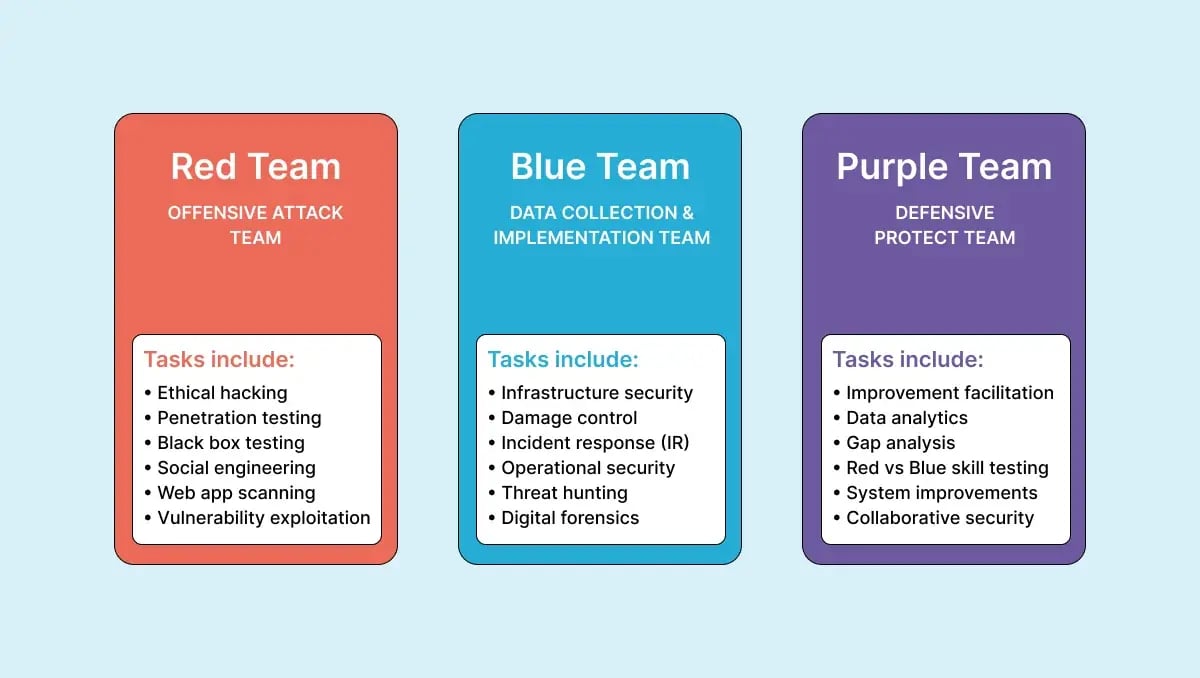
6. Red Team vs Blue Team
Penetration testers often use a military-inspired approach, with red teams acting as attackers and blue teams as defenders. This method makes tests more realistic, measuring not only weaknesses and threats but also how well the security team responds. Organizations sometimes hire experts for blue teams, but those with in-house security teams can use these exercises to upskill their employees.
This practice helps security teams:
- Learn to respond quickly to attacks
- Recognize what a real attack looks like
- Improve their ability to shut down attackers before they cause damage
There are different ways to conduct red and blue team tests:
- Blue teams may be given information about the attacker's plans or need to figure it out in real time.
- Blue teams might be informed about the timing of the simulation or kept in the dark.
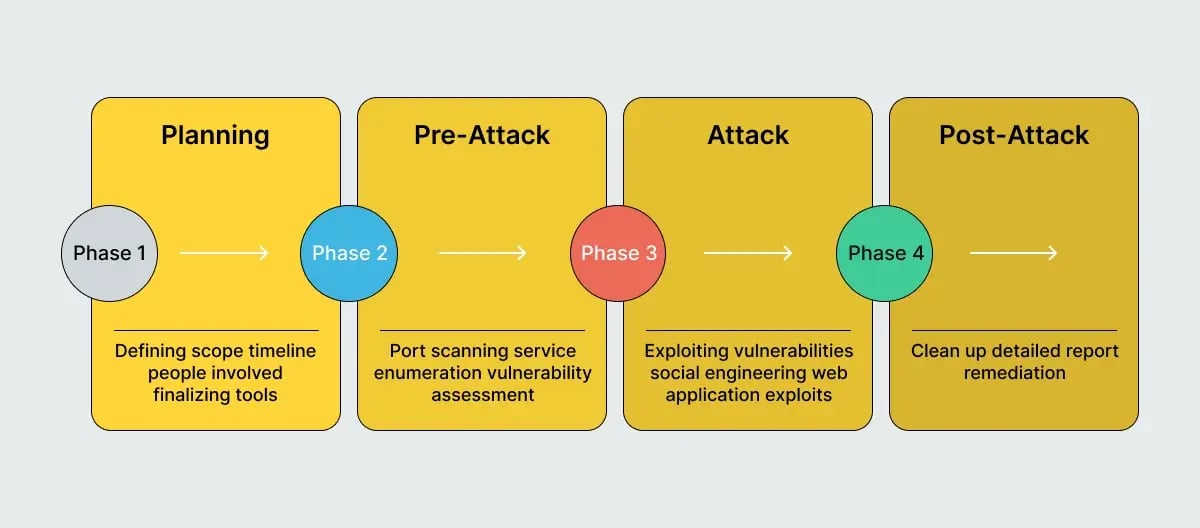
5 Steps to perform Penetration testing
While arranging a penetration test might seem overwhelming, following these steps can help make the process more manageable and ensure it goes smoothly.
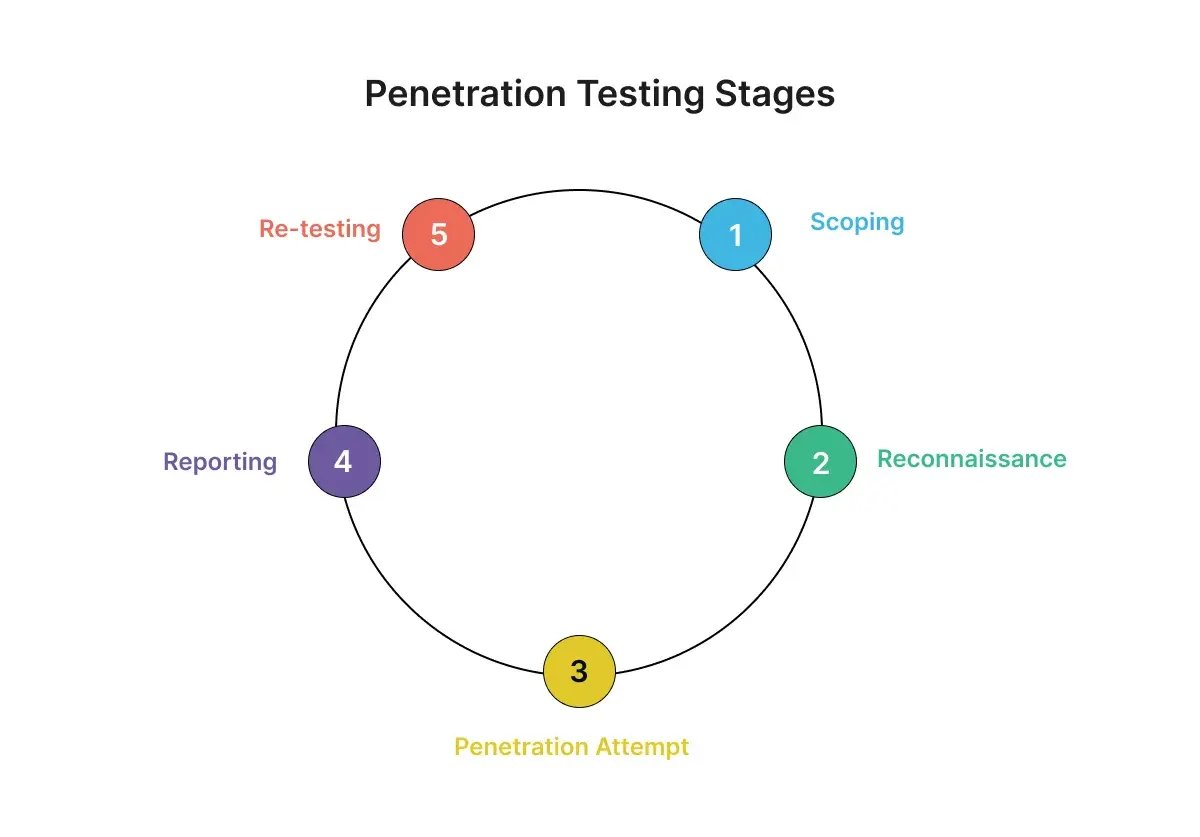
1. Scoping
Start by having stakeholders and hackers draft a pre-engagement contract. This document outlines the rules of engagement, the scope of your test and records testing priorities, timeframes, and methods. Signing this form provides legal proof of approval and protects the pen tester legally after hacking into the client’s systems.
2. Reconnaissance
Both penetration tests and real data breaches begin with reconnaissance. In this phase, the organization chooses who will conduct the test and which systems to focus on. Any planning concerns are handled in this phase. The tester will collect information from internal and external sources through:
- Internet searches
- Domain registration retrieval
- Known application vulnerabilities
- Network scanning
- Social engineering
3. Penetration Attempt
Once they have the necessary information, testers will attempt to exploit your system. This step demonstrates how far an outside hacker can go, including:
- Deleting, changing, or stealing private data
- Transferring company funds
- Copying customer account information
- Damaging the company’s reputation via social media or web changes
4. Reporting
After accessing your network, testers compile their findings into a report. This document offers a detailed view of how they infiltrated your system, the security weaknesses discovered, and recommendations to fix those vulnerabilities.
After you receive the report, pay special attention to:
- Specific weaknesses exploited
- Tools used to exploit them
- Data accessed (and what couldn’t be accessed)
- Time undetected
- Significant hurdles faced
- Ineffective security measures
5. Re-testing
When the first four steps are finished, you should review the tester’s findings and update your system. After you implement the pen tester's recommendations to fortify your environment, consider hiring the same pen tester to re-test it. With this approach, you can confirm that you adequately addressed their findings.
Companies should re-test their systems regularly to achieve compliance with some frameworks. For example, PCI requires two penetration tests a year or after making major changes. Major changes include OS changes, new firewall software, or moving data to the cloud.
How often should you perform penetration testing?
- Start-ups or small companies: Annual penetration testing for regular vulnerability identification and compliance adherence.
- Organizations handling sensitive data or facing elevated risks (e.g., healthcare, government, finance): Consider quarterly testing for strategic risk management and compliance.
- Large organizations with complex networks or continuous tech development: Quarterly testing to address evolving security challenges and rapid vulnerability introduction.
- Companies with high-risk tolerance or operating in heavily regulated sectors: Opt for continuous or on-demand testing for comprehensive protection despite resource intensiveness.
How can Global App Testing help you?
Global App Testing (GAT) specializes in functional bug identification, payment testing, and UX issue resolution. While we don't offer traditional penetration testing, GAT can still significantly boost your app's security with:
- Scalable crowdsourced testing – Combines scalability with detailed analytics and a comprehensive testing suite, efficiently covering various devices, operating systems, and markets.
- Global network of testers – With over 90,000 professional testers worldwide, we ensure thorough testing under real-world conditions.
- Streamlined testing process – Clients set the testing tasks, which are then matched to appropriate testers. Real-time feedback and reports enable quick issue resolution.
- Quality Assurance – We validate each bug report and feedback item for accuracy and relevance, providing actionable data for our clients.
Additionally, Global App Testing is committed to data integrity, availability, and confidentiality. We achieved ISO 27001 Certification in 2023, and our operations on AWS leverage advanced security architecture, robust encryption protocols, and authentication mechanisms to safeguard your data.
If you are interested in finding out more about our services, let’s schedule a call today!
We can help you drive software testing as a key initiative aligned to your business goals
Keep learning
5 iOS app testing tools to consider
iOS App Testing Guide to Ensure Functional Apps
How to Run a Comprehensive Mobile App Test [Guide]

